Ref: https://www.owasp.org/index.php/OWASP_Top_Ten_Cheat_Sheet
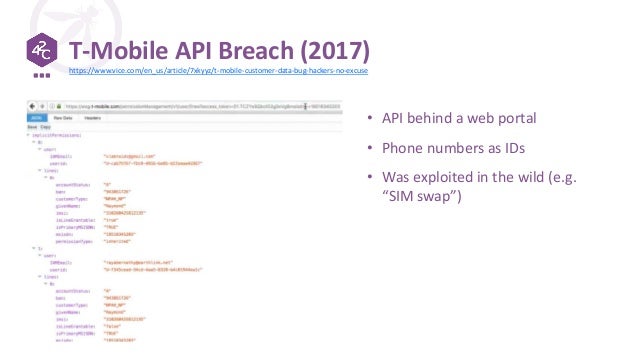

REST Security Cheat Sheet¶ Introduction¶. REST (or REpresentational State Transfer) is an architectural style first described in Roy Fielding's Ph.D. Dissertation on Architectural Styles and the Design of Network-based Software Architectures. It evolved as Fielding wrote the HTTP/1.1 and URI specs and has been proven to be well-suited for developing distributed hypermedia applications. The primary goal of the OWASP API Security Top 10 is to educate those involved in API development and maintenance, for example, developers, designers, architects, managers, or organizations. In the Methodology and Data section, you can read more about how this first edition was created.


| Presentation | Controller | Model | Testing (OWASP Testing Guide V3) | |
| A1 Injection | Render:
On Submit:
| Canonicalize using correct character setPositive input validation using correct character set(NR) Negative input validation. (LR) Sanitize input.Tip: updating a negative list (such as looking for “script”, “sCrIpT”, “ßCrîpt”, etc) will require expensive and constant deployments and will always fail as attackers work out your list of “bad” words. Positive validation is simpler, faster and usually more secure and needs updating far less than any other validation mechanism. | *Parameterized queries
Tip: All SQL Injection is due to dynamic SQL queries. Strongly consider prohibiting dynamic SQL queries within your organization | 4.8.5 SQL Injection (OWASP-DV-005)4.8.6 LDAP Injection (OWASP-DV-006)4.8.7 ORM Injection (OWASP-DV-007)4.8.8 XML Injection (OWASP-DV-008)4.8.9 SSI Injection (OWASP-DV-009)4.8.10 XPath Injection (OWASP-DV-010)4.8.11 IMAP/SMTP Injection (OWASP-DV-011)4.8.12 Code Injection (OWASP-DV-012)4.8.13 OS Commanding (OWASP-DV-013)4.8.14 Buffer overflow (OWASP-DV-014) |
| A2 XSS | Render:
On Submit:
| Canonicalize using correct character setPositive input validation using correct character set(NR) Negative input validation (LR) Sanitize inputTip: Only process data that is 100% trustworthy. Everything else is hostile and should be rejected. | Tip: Do not store data HTML encoded in the database. This prevents new uses for the data, such as web services, RSS feeds, FTP batches, data warehousing, cloud computing, and so on.Tip: Use OWASP Scrubbr to clean tainted or hostile data from legacy data | 4.8.1 Testing for Reflected Cross Site Scripting (OWASP-DV-001)4.8.2 Testing for Stored Cross Site Scripting (OWASP-DV-002)4.8.3 Testing for DOM based Cross Site Scripting (OWASP-DV-003)4.8.4 Testing for Cross Site Flashing (OWASP-DV004) |
| A3 Weak authentication and session management | Render:
| Design:
| Validate role is sufficient to create, read, update, or delete dataTip: Consider the use of a “governor” to regulate the maximum number of requests per second / minute / hour that this user may perform. For example, a typical banking user should not perform more than ten transactions a minute, and one hundred per second is dangerous and should be blocked. | 4.4.2 Testing for user enumeration (OWASP-AT-002)4.4.3 Testing for Guessable (Dictionary) User Account (OWASP-AT-003)4.4.4 Brute Force Testing (OWASP-AT-004)4.4.6 Testing for vulnerable remember password and pwd reset (OWASP-AT-006)4.4.5 Testing for bypassing authentication schema (OWASP-AT-005)4.4.7 Testing for Logout and Browser Cache Management (OWASP-AT-007)4.4.8 Testing for CAPTCHA (OWASP-AT-008)4.4.9 Testing Multiple Factors Authentication (OWASP-AT-009)4.4.10 Testing for Race Conditions (OWASP-AT-010)4.5.1 Testing for Session Management Schema (OWASP-SM-001)4.5.2 Testing for Cookies attributes (OWASP-SM-002)4.5.3 Testing for Session Fixation (OWASP-SM_003)4.5.4 Testing for Exposed Session Variables (OWASP-SM-004)4.5.5 Testing for CSRF (OWASP-SM-005)4.6.2 Testing for bypassing authorization schema (OWASP-AZ-002)4.6.3 Testing for Privilege Escalation (OWASP-AZ-003) |
| A4 Insecure Direct Object Reference | If data is from internal trusted sources, no data is sent.OrRender:
| Obtain data from internal, trusted sources.OrObtain direct value from random access reference access map. | Validate role is sufficient to create, read, update, or delete data. | 4.6.1 Testing for Path Traversal (OWASP-AZ-001) |
| A5 Cross Site Request Forgery | Pre-render:
Render:
|
Macos catalina download on windows. Tip: CSRF is always possible if there is XSS, so make sure XSS is eliminated within your application. | Validate role is sufficient to create, read, update, or delete data | 4.5.5 Testing for CSRF (OWASP-SM-005) |
| A6 Security Misconfiguration | Ensure web servers and application servers are hardened.PHP: Ensure allow_url_fopen and allow_url_include are both disabled in php.ini. Consider the use of Suhosin extension | Ensure web servers and application servers are hardenedXML: Ensure common web attacks (remote XSLT transforms, hostile XPath queries, recursive DTDs, and so on) are protected by your XML stack. Do not hand craft XML documents or queries – use the XML layer. | Ensure database servers are hardened | 4.2.6 Analysis of Error Codes (OWASP-IG-006)4.3.2 DB Listener Testing (OWASP-CM-002)4.3.3 Infrastructure Configuration Management Testing (OWASP-CM-003)4.3.4 Application Configuration Management Testing (OWASP-CM-004)4.3.5 Testing for File Extensions Handling (OWASP-CM-005)4.3.6 Old, Backup and Unreferenced Files (OWASP-CM-006)4.3.7 Infrastructure and Application Admin Interfaces (OWASP-CM-007)4.3.8 Testing for HTTP Methods and XST (OWASP-CM-008) |
| A7 Insufficient Cryptographic Storage | Design:
Render:
| Design:
Tip: Only certain personally identifiable information and sensitive values MUST be encrypted. Encrypt data that would be embarrassing or costly if it was leaked or stolen. Tip: It is best to encrypt data on the application server, rather than the database server. | Design:Tip: Do not use RDBMS database, row or table level encryption. The data can be retrieved in the clear by anyone with direct access to the server, or over the network using the application credentials. It might even traverse the network in the clear despite being “encrypted” on disk. | |
| A8 Failure to Restrict URL access | Design:
Pre-render:
Render:
|
Tip: It’s impossible to control access to secured resources that the web application server does not directly serve. Therefore, PDF reports or similar should be served by the web application server using binary octet streaming. Tip: Assume attackers will learn where “hidden” directories and “random” filenames are, so do not store these files in the web root, even if they are not directly linked. | Validate role is sufficient to create, read, update, or delete data | 4.4.5 Testing for bypassing authentication schema (OWASP-AT-005)4.6.1 Testing for Path Traversal (OWASP-AZ-001)4.6.2 Testing for bypassing authorization schema (OWASP-AZ-002) |
| A9 Insufficient Transport Layer Protection |
Tip: Use TLS 1.2 always – even internally. Most snooping is done within corporate networks – and it is as easy and unethical as fishing with dynamite. |
|
| 4.3.1 SSL/TLS Testing (OWASP-CM-001)4.4.1 Credentials transport over an encrypted channel (OWASP-AT-001) |
| A10 Unvalidated Redirects and Forwards |
or Render:
|
or
|
|
Ref: https://www.owasp.org/index.php/OWASP_Top_Ten_Cheat_Sheet

Owasp Api Top 10 Cheat Sheet 2020
| Presentation | Controller | Model | Testing (OWASP Testing Guide V3) | |
| A1 Injection | Render:
On Submit:
| Canonicalize using correct character setPositive input validation using correct character set(NR) Negative input validation. (LR) Sanitize input.Tip: updating a negative list (such as looking for “script”, “sCrIpT”, “ßCrîpt”, etc) will require expensive and constant deployments and will always fail as attackers work out your list of “bad” words. Positive validation is simpler, faster and usually more secure and needs updating far less than any other validation mechanism. | *Parameterized queries
Tip: All SQL Injection is due to dynamic SQL queries. Strongly consider prohibiting dynamic SQL queries within your organization | 4.8.5 SQL Injection (OWASP-DV-005)4.8.6 LDAP Injection (OWASP-DV-006)4.8.7 ORM Injection (OWASP-DV-007)4.8.8 XML Injection (OWASP-DV-008)4.8.9 SSI Injection (OWASP-DV-009)4.8.10 XPath Injection (OWASP-DV-010)4.8.11 IMAP/SMTP Injection (OWASP-DV-011)4.8.12 Code Injection (OWASP-DV-012)4.8.13 OS Commanding (OWASP-DV-013)4.8.14 Buffer overflow (OWASP-DV-014) |
| A2 XSS | Render:
On Submit:
| Canonicalize using correct character setPositive input validation using correct character set(NR) Negative input validation (LR) Sanitize inputTip: Only process data that is 100% trustworthy. Everything else is hostile and should be rejected. | Tip: Do not store data HTML encoded in the database. This prevents new uses for the data, such as web services, RSS feeds, FTP batches, data warehousing, cloud computing, and so on.Tip: Use OWASP Scrubbr to clean tainted or hostile data from legacy data | 4.8.1 Testing for Reflected Cross Site Scripting (OWASP-DV-001)4.8.2 Testing for Stored Cross Site Scripting (OWASP-DV-002)4.8.3 Testing for DOM based Cross Site Scripting (OWASP-DV-003)4.8.4 Testing for Cross Site Flashing (OWASP-DV004) |
| A3 Weak authentication and session management | Render:
| Design:
| Validate role is sufficient to create, read, update, or delete dataTip: Consider the use of a “governor” to regulate the maximum number of requests per second / minute / hour that this user may perform. For example, a typical banking user should not perform more than ten transactions a minute, and one hundred per second is dangerous and should be blocked. | 4.4.2 Testing for user enumeration (OWASP-AT-002)4.4.3 Testing for Guessable (Dictionary) User Account (OWASP-AT-003)4.4.4 Brute Force Testing (OWASP-AT-004)4.4.6 Testing for vulnerable remember password and pwd reset (OWASP-AT-006)4.4.5 Testing for bypassing authentication schema (OWASP-AT-005)4.4.7 Testing for Logout and Browser Cache Management (OWASP-AT-007)4.4.8 Testing for CAPTCHA (OWASP-AT-008)4.4.9 Testing Multiple Factors Authentication (OWASP-AT-009)4.4.10 Testing for Race Conditions (OWASP-AT-010)4.5.1 Testing for Session Management Schema (OWASP-SM-001)4.5.2 Testing for Cookies attributes (OWASP-SM-002)4.5.3 Testing for Session Fixation (OWASP-SM_003)4.5.4 Testing for Exposed Session Variables (OWASP-SM-004)4.5.5 Testing for CSRF (OWASP-SM-005)4.6.2 Testing for bypassing authorization schema (OWASP-AZ-002)4.6.3 Testing for Privilege Escalation (OWASP-AZ-003) |
| A4 Insecure Direct Object Reference | If data is from internal trusted sources, no data is sent.OrRender:
| Obtain data from internal, trusted sources.OrObtain direct value from random access reference access map. | Validate role is sufficient to create, read, update, or delete data. | 4.6.1 Testing for Path Traversal (OWASP-AZ-001) |
| A5 Cross Site Request Forgery | Pre-render:
Render:
|
Tip: CSRF is always possible if there is XSS, so make sure XSS is eliminated within your application. | Validate role is sufficient to create, read, update, or delete data | 4.5.5 Testing for CSRF (OWASP-SM-005) |
| A6 Security Misconfiguration | Ensure web servers and application servers are hardened.PHP: Ensure allow_url_fopen and allow_url_include are both disabled in php.ini. Consider the use of Suhosin extension | Ensure web servers and application servers are hardenedXML: Ensure common web attacks (remote XSLT transforms, hostile XPath queries, recursive DTDs, and so on) are protected by your XML stack. Do not hand craft XML documents or queries – use the XML layer. | Ensure database servers are hardened | 4.2.6 Analysis of Error Codes (OWASP-IG-006)4.3.2 DB Listener Testing (OWASP-CM-002)4.3.3 Infrastructure Configuration Management Testing (OWASP-CM-003)4.3.4 Application Configuration Management Testing (OWASP-CM-004)4.3.5 Testing for File Extensions Handling (OWASP-CM-005)4.3.6 Old, Backup and Unreferenced Files (OWASP-CM-006)4.3.7 Infrastructure and Application Admin Interfaces (OWASP-CM-007)4.3.8 Testing for HTTP Methods and XST (OWASP-CM-008) |
| A7 Insufficient Cryptographic Storage | Design:
Render:
| Design:
Tip: Only certain personally identifiable information and sensitive values MUST be encrypted. Encrypt data that would be embarrassing or costly if it was leaked or stolen. Tip: It is best to encrypt data on the application server, rather than the database server. | Design:Tip: Do not use RDBMS database, row or table level encryption. The data can be retrieved in the clear by anyone with direct access to the server, or over the network using the application credentials. It might even traverse the network in the clear despite being “encrypted” on disk. | |
| A8 Failure to Restrict URL access | Design:
Pre-render:
Render:
|
Tip: It’s impossible to control access to secured resources that the web application server does not directly serve. Therefore, PDF reports or similar should be served by the web application server using binary octet streaming. Tip: Assume attackers will learn where “hidden” directories and “random” filenames are, so do not store these files in the web root, even if they are not directly linked. | Validate role is sufficient to create, read, update, or delete data | 4.4.5 Testing for bypassing authentication schema (OWASP-AT-005)4.6.1 Testing for Path Traversal (OWASP-AZ-001)4.6.2 Testing for bypassing authorization schema (OWASP-AZ-002) |
| A9 Insufficient Transport Layer Protection |
Tip: Use TLS 1.2 always – even internally. Most snooping is done within corporate networks – and it is as easy and unethical as fishing with dynamite. |
|
| 4.3.1 SSL/TLS Testing (OWASP-CM-001)4.4.1 Credentials transport over an encrypted channel (OWASP-AT-001) |
| A10 Unvalidated Redirects and Forwards |
Render:
|
or
|
|
